Shield Sphere
Unified Business Resilient Security & Operation Center
Consolidate your entire security stack SIEM, SOAR, IOC & threat intelligence, AI-powered Query builder, compliance automation into a single intelligent command center.
Replace 5-15 fragmented tools with one platform that detects threats in real-time, automates incident response, and maintains continuous compliance.
Deploy in 4 hours. Reduce costs by 50%. Gain visibility that protects.
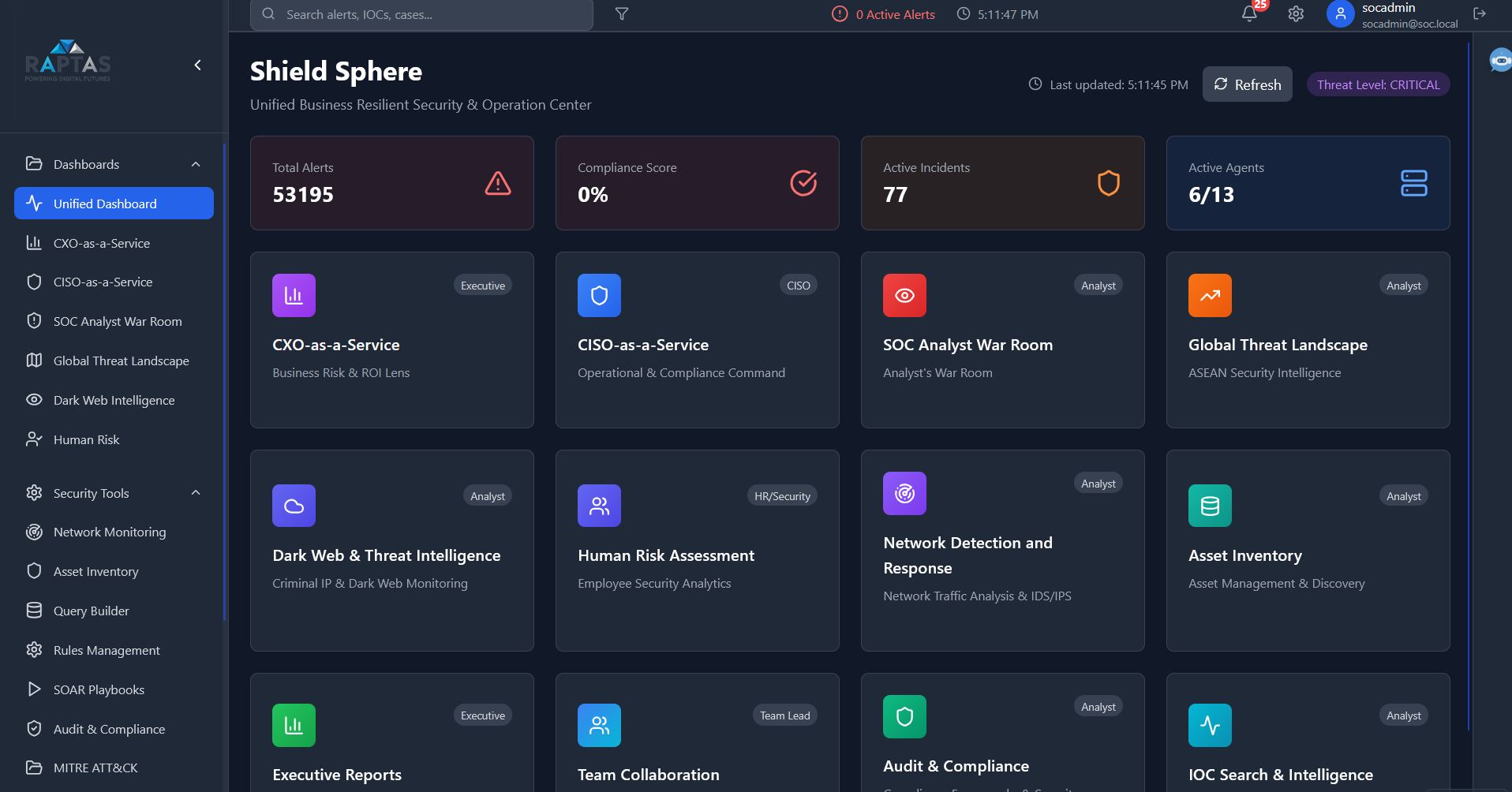
Unified Security Dashboard
Core Modules
Every feature designed to eliminate complexity, accelerate response, and unify your security operations.
One Dashboard. Every Role. Complete Visibility.
Shield Sphere's unified dashboard eliminates the chaos of jumping between 15 different tools. Whether you're a CISO managing operational risk, a SOC analyst triaging live threats, or a CXO tracking business impact, everyone works from one intelligent command center.
Key Features
Role-based views tailored for CXO, CISO, and SOC teams
Real-time security posture across all assets and controls
Consolidated alerts and workflows from multiple security tools
Executive Command Center
The Executive Security Snapshot distills posture, risks, ROI, and trends into a concise leadership view. It highlights top business risks by impact, demonstrates the value of security investments, and provides prioritized recommendations with ownership. Mini trends and outlooks capture emerging patterns, enabling executives to act with clarity and foresight.
Key Features
Business risk prioritization with financial impact analysis
Security investment ROI tracking and reporting
Strategic trend analysis with actionable executive insights
SOC Analyst War Room
The SOC Analyst War Room is a real-time hub for detection and response. Analysts access queues, triage, and MITRE mapping with priority indicators guiding focus. Metrics track SLA compliance and response times, while advanced triage views, threat intelligence, and playbooks enable decisive action to contain threats quickly.
Key Features
Priority-based alert queues with MITRE ATT&CK mapping
Integrated playbooks for rapid incident response
SLA tracking with real-time performance metrics
CISO Control Panel
The CISO Control Panel centralizes compliance, audits, incidents, risk oversight, industry benchmark, Cyber news etc. It tracks posture across domains, monitors violations, and provides a live incident pipeline with SLA performance. Asset risk registers and control coverage highlight priorities, while the evidence locker and board report ensure governance and executive alignment.
Key Features
Compliance posture tracking across multiple frameworks
Evidence locker with audit-ready documentation
Board-ready reporting with risk and control insights
Threat Intelligence
The Threat Intelligence module centralizes IOC and feed management. Users can search across IPs, domains, and file hashes with filters and tags for faster correlation. IOC records provide enriched context, while feed management ensures sources stay updated. Metrics highlight high-confidence threats, and audit trails guarantee traceability.
Key Features
Multi-source IOC aggregation and enrichment
Advanced correlation across IPs, domains, and file hashes
Automated threat feed updates with confidence scoring
Global Threat Landscape
The Global Threat Landscape module provides a comprehensive view of threat patterns across different geographic regions. It analyzes and visualizes global attack trends, threat actor activities, and emerging vulnerabilities specific to each region. This intelligence enables organizations to anticipate and defend against region-specific threats with targeted security measures and proactive risk mitigation strategies.
Key Features
Geographic threat intelligence with regional attack patterns
Threat actor profiling by region and campaign
Regional vulnerability trends and emerging threat analysis
Query Builder
The Query Builder transforms plain language into structured security searches. Predefined categories accelerate investigations, while results summarize events, severity, and performance. AI analysis highlights key findings in plain terms, and recent examples link directly to impacted assets. It enables teams to move seamlessly from question to action.
Key Features
Natural language query processing with AI assistance
Pre-built investigation templates for common scenarios
Direct asset linking from search results to action
Human Risk Assessment
The Human Risk Assessment module evaluates and monitors security risks posed by human behavior and user activities. It analyzes user patterns, identifies risky behaviors, and provides targeted training recommendations to reduce human-related security incidents. The module tracks user security awareness levels, phishing susceptibility, and compliance with security policies to create a comprehensive view of organizational human risk.
Key Features
Behavioral analysis and risk scoring for users and departments
Phishing simulation and security awareness tracking
Targeted training recommendations based on individual risk profiles
SOC Case Management
The SOC Case Management module streamlines security incident tracking and resolution workflows. It provides a centralized platform for creating, assigning, and managing security cases from detection through remediation. The module tracks case status, priority levels, and response times while maintaining detailed audit trails and enabling seamless collaboration between SOC team members to ensure efficient incident response and resolution.
Key Features
Centralized case tracking with priority-based workflows
Automated case assignment and escalation rules
Detailed audit trails and SLA monitoring for incident response
Audit & Compliance
The Audit and Compliance module unifies scoring, frameworks, and audit readiness. Dashboards highlight compliance trends, while framework and control sections provide detailed tracking with evidence attachments. Assessments monitor remediation progress, and audit trails with an evidence locker ensure accountability and readiness for regulatory or board reviews.
Key Features
Multi-framework compliance tracking (ISO 27001, PCI DSS, HIPAA, GDPR)
Automated evidence collection and audit trail generation
Remediation workflow management with progress tracking
Dark Web & Threat Intelligence
The Dark Web and Threat Intelligence module provides a specialized hub for monitoring external threats. Metrics summarize alerts and risk IPs, while multi-type lookups enable rapid investigations. Graphical panels show timelines and severity, network metrics reveal anonymized traffic, and live feeds highlight high-risk threats. System recommendations ensure coverage remains optimized.
Key Features
Continuous dark web monitoring for compromised credentials
Real-time threat intelligence feeds and risk scoring
Network anomaly detection with anonymized traffic analysis
Executive Reports
The Executive Reports module acts as a governance hub, consolidating strategic, compliance, and operational reporting into one environment. It delivers scheduled board-level summaries, multi-framework compliance reports, and daily security performance metrics, all mapped to industry standards. Automation ensures consistent delivery, while quick actions streamline scheduling and access. A dedicated board report provides a 30‑day view of compliance, risks, and investments, supported by KPIs and risk indicators that guide executive decision-making with clarity and accountability.
Key Features
Automated board-level reporting with 30-day compliance snapshots
Multi-framework compliance status across all standards
Executive KPI dashboards with risk and investment tracking
Why Shield Sphere?
The intelligent security platform that transforms complexity into clarity
Deploy in 4 Hours
Not 6 months. Pre-configured, battle-tested deployment that gets you operational on day one.
50% Cost Reduction
Replace 5-15 tools with one platform. Cut licensing, training, and integration costs in half.
Unified Visibility
One dashboard for CISO, SOC, compliance, and executives. Everyone sees what matters to them.
AI-Powered
Plain-language queries, automated threat detection, and intelligent response recommendations.
Compliance Ready
Built-in frameworks for ISO 27001, PCI DSS, HIPAA, GDPR with automated evidence collection.
24/7 Protection
Continuous monitoring, dark web surveillance, and real-time threat intelligence integration.
Built-In Compliance Frameworks
Automated compliance monitoring and reporting across industry standards
ISO 27001
PCI DSS v4.0
NIST CSF 2.0
SOC 2
HIPAA
SWIFT CSP
Industries We Protect
As a unified SOC platform, Shield Sphere delivers enterprise-grade security operations across every regulated industry.
Frequently Asked Questions
Everything you need to know about Shield Sphere.
Stop Juggling Tools.
Start Winning Battles.
See Shield Sphere in action. Schedule a personalized demo and discover how we consolidate your entire security operation into one intelligent command center.